Image Name: 1714798_634978548101937500.jpg
File Size: 652 x 652 pixels (27025 bytes)
Image Name: home images network security policy paper network security policy ...
File Size: 1240 x 1240 pixels (126475 bytes)
Image Name: NIST Cyber Security Example Tier Model
File Size: 550 x 550 pixels (32768 bytes)
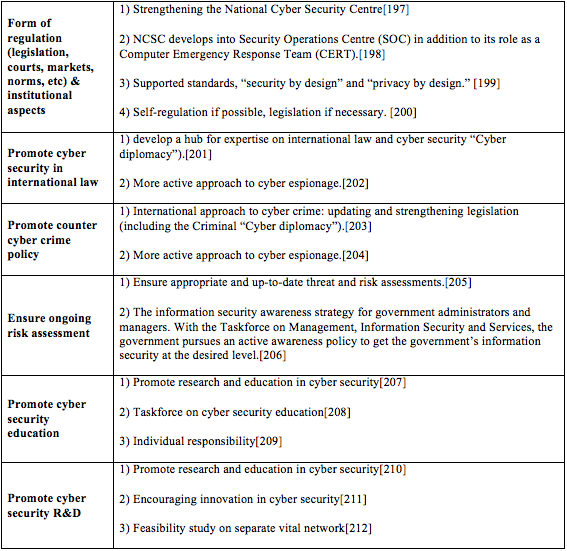
Image Name: ... Cyber Security Strategy (NCSS), “The Ministry of Security and
File Size: 567 x 567 pixels (102603 bytes)
Image Name: Protection from cyber threats
File Size: 595 x 595 pixels (98748 bytes)
Image Name: ... security program are prerequisites for purchasing cyber insurance
File Size: 1000 x 1000 pixels (195675 bytes)
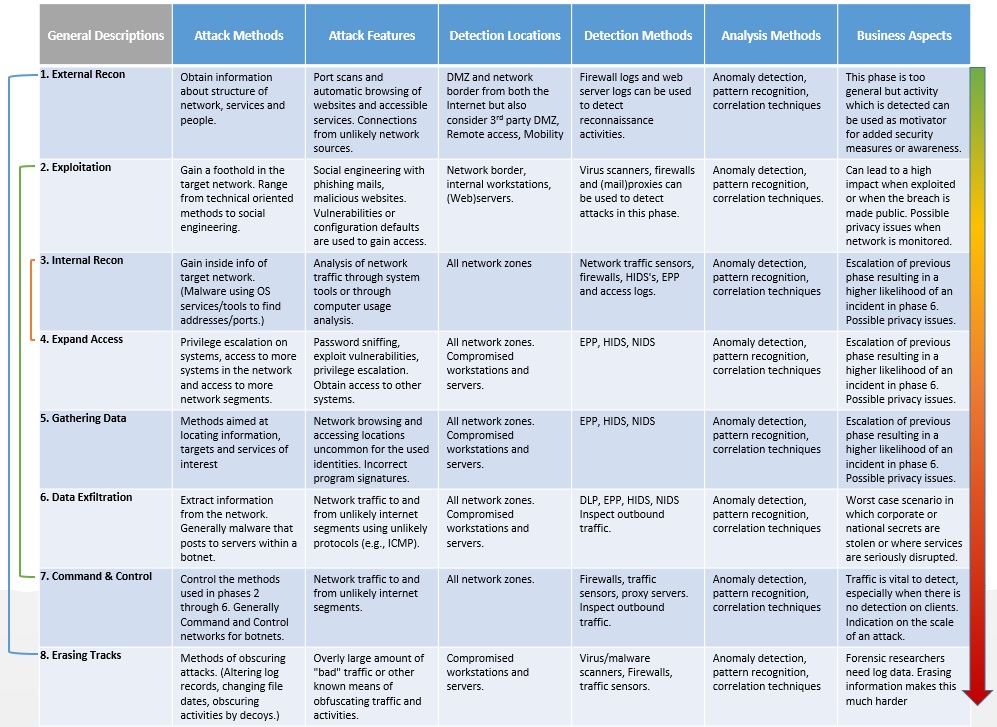
Image Name: APT Detection Framework - General Descriptions
File Size: 997 x 997 pixels (262985 bytes)
Image Name: Acceptable Use Policy specifies policy for the use of information ...
File Size: 150 x 150 pixels (12778 bytes)
Information Management and Cyber Security Policy
7 policy follows the framework of ISO17799 for Security Policy guidelines and is consistent with existing SUNY Fredonia policies, rules and standards.. Information Technology Cyber Security Policy - Illinois.gov: Information Technology Cyber Security Policy (Insert Name of Organization) (Insert Date) SAMPLE TEMPLATE Organizations are encouraged to develop their own policy and. sample security policies - SANS Information Security Training: Free information security policy templates courtesy of the SANS Institute, Michele D. Guel, and other information security leaders.. STATE OF ALABAMA - Cyber Security - Search Policies: Search Policies Please type your keyword(s) into the box below and click the "Search" button. Applicability Unless specifically noted otherwise, the following .... Effective cyber security to combat crime and protect data ...: Executives should lead by example and attend cyber security training programs. ... for example by circulating a friendly and fun email quiz about a security policy.. Cybersecurity Policy Making at a Turning Point - OECD: cybersecurity policy debates. For example, in some countries, the co-ordination ... As cyber-security policy develops, the intersections between the sovereignty and. Information Security Policy - Mass.Gov: Cyber Security; Security for State ... (for example, personal information ... Agencies are required to review the adopted Information Security Policy annually at a .... Security Breach Examples and Practices to Avoid Them: Security Breach Examples and Practices to ... including an individual’s health insurance policy number or subscriber ... National Cyber Security Awareness Month;. Cyber Security Law & Policy Graduate Level Course: Online course on Cyber Security Law and Policy from Syracuse University's Institute for National Security and Counter-terrorism.. What is cybersecurity? - Definition from WhatIs.com: Cybersecurity is the body of technologies, processes and practices designed to protect networks, computers, programs and data from attack, damage or unauthorized access.
Image Name: NIST cybersecurity framework analysis: Putting it to good use
File Size: 580 x 580 pixels (146169 bytes)
Image Name: Cyber Security Market is Growing at a CAGR of 11.3% and to Reach $120 ...
File Size: 587 x 587 pixels (25947 bytes)
Related Keyword:
1714798_634978548101937500.jpg, home images network security policy paper network security policy ..., NIST Cyber Security Example Tier Model, ... Cyber Security Strategy (NCSS), “The Ministry of Security and, Protection from cyber threats, ... security program are prerequisites for purchasing cyber insurance, APT Detection Framework - General Descriptions, Acceptable Use Policy specifies policy for the use of information ..., NIST cybersecurity framework analysis: Putting it to good use, Cyber Security Market is Growing at a CAGR of 11.3% and to Reach $120 ....
No comments:
Post a Comment